Some users also share links on encrypted apps like Telegram or Keybase that you can check. Hence, if you participate in them, whether knowingly or unknowingly, you can end up putting criminal charges on yourself, and in some extreme cases, even imprisonment. It is a hub for financial cybercrime and offers a wide range of illicit services and stolen data that cater to sophisticated cybercriminals.

Hidden Wallet
A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically. Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.
- Privacy-focused operators are shifting to Monero due to its default anonymity, compared to Bitcoin’s transparent ledger Darknet markets see BTC inflow drop to $2B.
- The clearnet is the regular internet you’re used to using, where network traffic origins are fairly easy to pinpoint.
- Some users are in the forums trying to engage in smear campaigns against the competing forums.
- Bohemia popped up post-Hydra takedown and brings a fresh vibe—drugs (weed, pills, some coke) and digital goodies like hacked logins, no exact listing count, but it’s growing fast.
- It works by sending internet traffic through volunteer-operated nodes all over the world.
- The Dark Web and Darknets offer valuable spaces if you value privacy, freedom of speech, or research security technologies.If you misuse them, the consequences can be severe.
What Are Darknets & Dark Markets?
It is one of the best sites on the dark web to find your favorite comics. Sci-hub has more than 80 million research documents, and more than 80% of the database contains journal research articles. Since these pages would otherwise be behind paywalls, it stands to reason that this would go against copyright laws. The Imperial Library currently holds around 1.5 million books, some of which may be hosted illegally, and thus, their consumption might violate copyright laws. To protect yourself against any legal repercussions, you should consider using NordVPN. Therefore, you will always find updated search results while using this service.
Topics And Products Sold
The most interesting thing about NordVPN is its built-in Onion over VPN feature. It encrypts your traffic at the entry node and changes your IP address. This means you will get a VPN’s security and enjoy the anonymity of the Tor network simultaneously.
What Cybersecurity Surprises Does 2018 Hold?
- Instead, you can use a VPN to spoof your internet connection to somewhere completely different, such as Poland.
- It is considered very secure thanks to strict user validations and transparent payment and vendor review procedures.
- Altenen is probably the legend when it comes to the world of online fraud – it has been around for a long time.
- It provides them with valuable information needed to carry out a variety of attacks.
- Tools like Tor are used to bypass government-imposed firewalls and surveillance, ensuring open communication.
SecureDrop is a popular site where whistleblowers can anonymously share confidential information with journalists. Since it’s hosted on the Tor network, dark web users don’t have to worry about being tracked or their personal information being revealed while exchanging information with media outlets. Cryptocurrencies weren’t so popular among the general public until recently. However, dark web users have relied on Bitcoin transactions for over a decade, as they allow people to make payments while staying completely anonymous. And Hidden Wallet is one of your best options if you’re looking for a Bitcoin wallet for use on the dark web. Hackers spend a lot of time on the dark web, and it’s not too difficult to get access to hacking tools and data leaks in this part of the internet.
Best Dark Web Sites In 2025 (Unseen Onion, Tor Links)
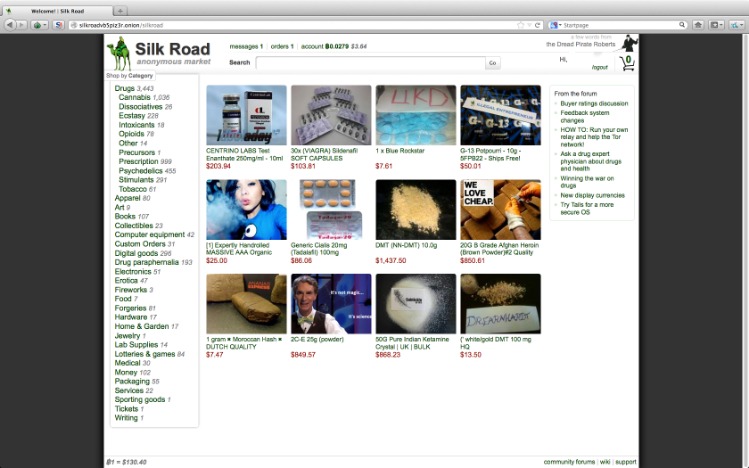
If you wanted to become a seller on the website, entry is open, and the marketplace will take a 2% commission on every sale with a vendor bond varying between the $0 and $250 mark. There are plenty of safety precautions as well to help protect customers. These include the ‘Vendor Warning System,’ a feature that will notify you if a vendor you’re looking at or buying from is potentially involved in a scam sale. Below, we’re going to explore eight of the most popular Darknet markets that are currently available right now, helping you to identify what’s out there, and get to know a bit more about each one. Even if someone does try to track you, they’re going to be taken to a random part of the world where don’t exist, rather than your computer and internet address in the real world.
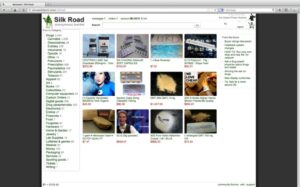
Biggest Dark Web Marketplaces
It has been in operation for more than a decade since its debut in 2014. Brian’s Club is one of the best place to buy stolen credit card info, including CVVs, dumps, and even full account packages without revealing your identity. From items like drugs, fake ID cards, and hacked bank accounts to more complex offerings like human trafficking, these sites carry all the illegal activities you can think of.

Radar Rundown Free firewall software allow privacy ethusuiasts to secure their network and block mal… We recommend installing a premium antivirus program for optimal protection against malware infections. We also made sure to select only sites that have been around for a considerable amount of time without being taken down or being the subject of any privacy or security scandals. The Tor browser option for streaming comes with eleven channels with varying genres. But, honestly, if you are going on the dark just to enjoy free music, we recommend that you go for free torrent platforms on the surface web instead.
With ZeroBin, you can easily exchange encrypted messages within the dark web. With 256-bit AES encryption, this platform enforces its two-fold service of secure messaging and zero logs of your activity. SecureDrop is a secure hub for journalists and whistleblowers to interact and trade vital information. Platforms like SecureDrop allow these carriers of truth to evade tracking. It protects their submissions using high-end encryption and doesn’t log their IP addresses or device information – full anonymity. ProPublica is a prominent investigative journalism platform on the regular and dark web.

Naval Research Laboratory mathematicians and computer scientists in the mid-1990s. The U.S. Army developed “onion routing” to protect intelligence communications online. That said, you may come across advertisements while searching on Haystack. Fortunately, you can upgrade to the premium version and avoid that altogether while accessing advanced searches and results from historical onion sites.
Is Claude Safe And Secure In 2025?
The advantages of I2P are based on a much faster and more reliable network. Additionally, I2P doesn’t rely on hidden directories that serve as a resource for .onion domains. I2P can only be used to access hidden sites that are only available on the I2P network.
The site seeks to liberate information by making it free to individuals and institutions. The website is available on the surface web and has a .onion site. This means you can visit the site anonymously using the Onion browser, especially if you live under an oppressive regime. Moreover, due to its popularity, many copycats of the Hidden Wiki exist.