
Today, many organizations exist that are created only to handle these reports anonymously and effectively. They know how to process the information and get it to the correct law enforcement agencies internationally. Simply put, accessing and browsing the dark web is perfectly legal. For example, it maintains your privacy and enables you to access untraceable content and services. Some of the deep web sites do not use standard top-level domains (TLD) such as .gov, .com, .net, etc.
Direct Payment Processing
This cryptographic approach ensures that only users with proper security knowledge can access the platform. The security layer incorporates multiple protection mechanisms including anti-phishing measures, DDoS protection, and advanced encryption for all user data and communications. Our security team continuously monitors for threats and implements proactive measures to protect user privacy and platform integrity. Our buyer protection policies include mandatory escrow for all transactions, dispute resolution procedures, and clear guidelines for order cancellations and refunds.
While its .onion address doesn’t make it much easier to maintain an anonymous account, it does make Facebook more accessible in places where it’s censored. Torch is one of the oldest and most popular onion search engines on the dark web, serving over 80,000 requests per day. Torch is funded primarily through advertising—purchased in BTC, of course—which is why you’ll find the front page blanketed with old-school banner ads of dubious origins. Haystak also offers a premium version that allows advanced search, access to historical content, and email alerts. Search engines on the dark web are a bit of a contradiction because dark web sites by definition are not indexed by traditional search engines.

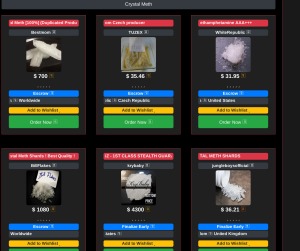
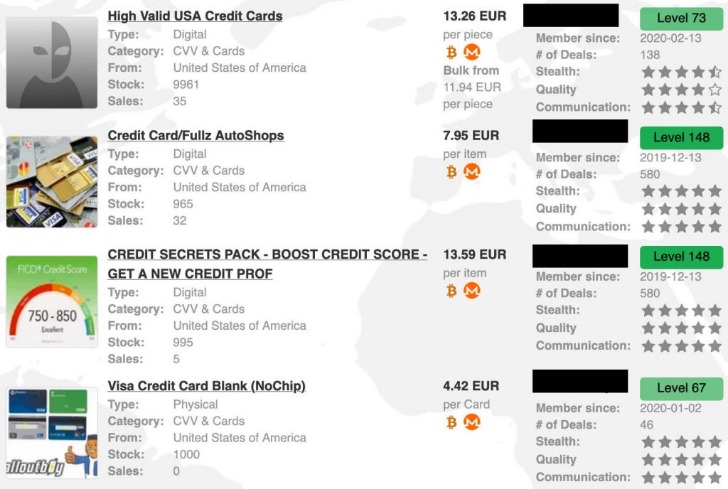
Bitcoin transactions benefit from our advanced mixing services, while Monero provides inherent privacy through its built-in anonymity features. All transactions are processed through our secure escrow system, ensuring buyer protection and vendor payment security. Dark markets, on the other hand, are platforms within darknets where illicit transactions occur. These marketplaces facilitate the exchange of everything from stolen credentials and drugs to weapons and hacking tools. The anonymity and encryption provided in dark markets create a haven for cybercriminals and nation-state actors to buy and sell dangerous assets while evading detection.
Ares Darknet Market
The Camouflage Mode is intended for people living in countries with heavy internet censorship, like China. It will make your VPN activities seem like normal traffic, so you can use an uncensored internet. However, this feature is only available on iOS, Android, and Windows.
The market facilitates trades in stolen credit card data, hacked bank accounts, and services to facilitate the laundering of cryptocurrency. Established in 2020, Awazon Market has quickly become one of the most famous darknet marketplaces. The market claims to provide secure and anonymous commerce services. You can find a lot of goods and services packed with stealth high-level encryption, no JavaScript, and anti-DDoS protection.
How Does The Dispute Resolution Process Work On Ares Market?
All packages must be shipped with appropriate stealth measures and tracking information. Vendors are responsible for secure packaging and timely delivery. Vendors must respond to customer inquiries within 24 hours and maintain professional, helpful communication throughout the transaction process.
Ares Market Onion Products
It was initially created to provide additional security and eliminate cryptocurrency theft. It’s a wallet, explorer service, not a dark web marketplace itself, but still a helpful resource. RiseUp is a top dark web website that offers secure email services and a chat option. It was created in 1999 as a secure communication platform for people and groups working on liberatory social change.
Dark Web Reveals Tech Companies Leak Most User Data
TRM Labs analysis shows that nearly half of the marketplaces launched in 2024 accepted only Monero — a sharp increase from just over one-third in 2023. This signals a growing preference among darknet operators for obfuscation and anti-surveillance tools. Cryptocurrency-enabled drug sales also grew by over 19% from 2023 to 2024, reaching nearly USD 2.4 billion in volume. Vendors need to have at least two years of experience, a feedback rate of 95% or higher, and 500 completed sales.
Top Markets
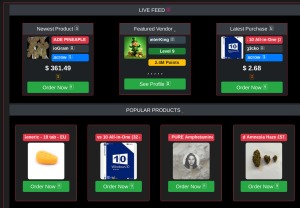
As terrible as its reputation may be, some vendors sell legitimate goods or services. Some customers even use the dark web to make anonymous purchases, especially in areas where privacy is a huge concern. So, not everyone who shops there is looking for something illegal. The site gives out free samples of the stolen data every now and then to gain more customers. With its fast rise to fame and focus on money fraud, it’s no surprise that cybersecurity experts are keeping a very close eye on this one.
Vendors must respond to customer inquiries within 24 hours and maintain courteous, helpful interactions. All communications must be conducted through encrypted channels with proper PGP implementation. Customer service excellence is monitored and factored into vendor ratings and platform standing. The MITRE ATT&CK framework provides a comprehensive view of adversary tactics. Singularity™ Threat Intelligence provides insights into adversary tactics and helps mitigate these risks before they impact your organization.
Activists and government critics prefer to remain anonymous, fearing repercussions if their identities are revealed. Besides, victims of crime may want to hide their identities from their perpetrators. Nonetheless, if whatever you do is deemed illegal in your country, you can get into trouble.
What Are Darknets & Dark Markets?
This is also why the sites on the dark web are called Tor links. From custom hardware to advanced software, we provide everything you need to dominate. The only listings that are not done through escrow are listings by FE vendors.FE vendors are vendors that have been proven to be reliable and reputable. Mobile access may cause issues with functionality, formatting, or security features.
- The process includes evidence submission periods, formal review phases, and binding resolution decisions that are enforced through our escrow system.
- Nowadays, many people use the Tor browser to surf the public internet and navigate the deeper parts anonymously.
- Many dark net sites do not undertake the necessary measures to protect users like most websites on the surface web.
- Daily deposits dropped by over 90% in the final weeks, despite reassurances from its administrator.
The only difference is that it passes your traffic through random nodes before reaching the destination. This means your activities cannot be traced or your browser history exposed. The early version of Tor was created to mask spy communications. In due course, the framework was remodeled and made public as a secure browser. Initially, the dark web was mainly used by government agencies, big businesses, hackers, and cybercriminals.



