Operating Tor is largely similar to operating a web browser such as Mozilla Firefox or Google Chrome. The anonymity offered by Tor allows both hosts and users to cloak their identities. By setting up the server correctly, hosts can even mask the location of their servers. Outlined below are the top five differences between the dark and deep web.
Is The Deep Web Or Dark Web Safe To Access?
- If your Social Security number is found on the dark web, take immediate action to protect yourself.
- If you think that search engines like Google (there are more!) know about everything on the internet, you’d be wrong.
- We understand the intricacies of deep web security and dark web risks, and we’ve tailored our technologies to shield you effectively.
- Surface web search engines do not index these sites, so you need the right tools to navigate safely and anonymously.
This will help you understand what type of attacks to be on the lookout for when you’re browsing online. Think about logging into your email or checking a paywalled article. The Deep Web is part of the vast, invisible chunk of the World Wide Web that search engines can’t crawl. Simple password access or subscription through paywalls often does the trick.
Get The Latest Cybersecurity News And Updates Sent Straight To Your Inbox
The surface web, what most users think of as “the internet,” represents only about 10% of total internet content. This visible portion includes all websites and resources that search engines can discover and index. It’s not easy to remove personal data from the Deep Web or Dark Web. Although most of this Deep Web can contain legitimate content that users can control with privacy settings and requests, much of the Dark Web contains data without the owners’ consent. People worrying about their data need to check their digital footprint periodically and seek services specifically offering data removal and monitoring services in order to minimize the potential risks. The deep web contains private networks used by business organizations, governmental departments, and educational institutions.
How To Access The Deep Web
She holds a Bachelor’s degree in Liberal Arts and a triple Master’s degree in Literary and Cultural Studies. Outside of work, she is a travel enthusiast, music lover and avid learner interested in global cultures, spirituality, psychology and neuroscience. The terms “dark web” and “deep web” are often conflated and used interchangeably, mainly because the former is part of the latter.
Read on to learn the pros and cons of the dark web, how to access it, and get tips for staying safe. Then, install Norton 360 Deluxe to get AI-powered scam detection to help secure your browsing against online threats. H25.io is a premium directory in the Tor network, offering access to a diverse and meticulously curated list of onion sites. Our mission is to simplify navigation in the complex and evolving world of the darknet. Here, you’ll find links to various resources, including educational archives, private forums, anonymous services, and more.
Building A Smart Security Pipeline
That includes not only obscure forums and leak sites, but also widely used developer platforms like GitHub, which have increasingly become a source of risk for modern organizations. The government and private companies utilize the deep web to store private information. This includes medical, legal records, private bank data, and so on. Any website that does not have a link to it can be considered to be a part of the deep web and it accounts for 90 percent of the web. Any time you log in to a website, the information you access is stored on the deep web. This can be your email, banking information, or your social media account.
For instance, Edward Snowden used the dark web to reveal that NSA surveils all US citizens, even if someone has no criminal history. And the dark web (aka darknet) is still a smaller section, up to 5% of the entire internet. Understanding the distinctions between the dark web and the deep web environments is essential for developing effective cybersecurity strategies. The dark web deep web difference is primarily in their accessibility methods and intended purposes. Furthermore, 31 new ransomware groups were discovered in 2024 (a 30% year-over-year rise in active ransomware groups).
Is The Deep Web Or Dark Web Illegal?
For instance, knowing if an organization’s data has been leaked can help security analysts change the relevant credentials and secure their systems before an attack occurs. It is tremendously more vast than the surface web, with some experts estimating that search engines index less than 1% of online content. While the content on the dark web has the potential to be more dangerous, this content is usually walled off from regular users. However, it is entirely possible for regular users to accidentally come across harmful content while browsing the deep web, which is much more easily accessible.
Surface Web Vs Deep Web Vs Dark Web: Differences Explained
TOR can access regular websites also, a website on this network has .onion address. Friend-to-Friend is another kind of darknet where two-person transfer data between them anonymously. Only concerned people have access to it and it is encrypted and password protected. Besides this, Freenet is also a darknet that is used for file transfer anonymously, there are many other darknets available. The deep web contains hidden content, such as private databases, government websites, and intranets. These parts of the internet require users to log in to access the data, and they consist of cloud servers that are protected with encryption and unlisted by search engines.
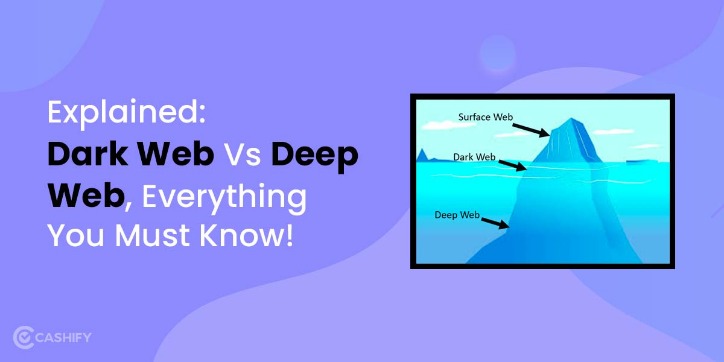
Understanding the differences between the deep web vs dark web is crucial for the safe and responsible use of the internet. Many useful services can be found in the deep web, including facilitating research in academia, securing sensitive medical information, and providing a means for private communication within organizations. These resources are essential for various professional fields and contribute positively to society.
While Tor protects you and gives you anonymity on the dark web, we recommend that you don’t use the dark web. If you still wish to access it, don’t use your regular email and ensure your Tor applications are updated. Avoid downloading files as they are often filled with viruses and malware.
Proactive monitoring and management of security threats to protect the organization’s assets. Endpoint protection solutions that provide strong security against cyber threats. When these two concepts aren’t clearly distinguished, it’s easy to fall into fear, misinformation, or even make serious mistakes when it comes to protecting your data. It would be a site that’s possibly reasonably designed, but they didn’t bother to register it with any of the search engines. The fact also remains that for better or worse, it is simply technically unfeasible to police the internet, all 60 trillion pages of it. It is even tougher for the law enforcement to monitor anonymizing networks like Tor.