ExpressVPN provides DNS leak protection that is helpful for protecting your privacy while you surf the dark web. The location is excellent for a VPN service as rules there are relaxed. CyberGhost provides its users with strong military grade 256-bit AES encryption, a Kill switch, and port forward secrecy. Because of this and other flaws, it is advisable to use another end-to-end encryption service preferably a VPN service to achieve maximum anonymity. Unlike Tor and I2P, a server is not needed to host content, and the content that you upload on Freenet stays there permanently. Even some sites like Facebook think so, and they will actually warn you that you should not do it if you try to access their .onion version.
Dark Web Sites

Its goal is to offer anonymous access to the content without being censored, no matter where you live. The good news is that the BBC Onion site is an international edition. As a result, it not only focuses on the UK but also provides worldwide news. Hence, if you participate in them, whether knowingly or unknowingly, you can end up putting criminal charges on yourself, and in some extreme cases, even imprisonment. If you know the right websites, you can easily access a tremendous amount of information, including research articles, news stories, and more.
- Instead, you often have to consult directories to find lists of legitimate sites and visit and access them that way or use special dark web-friendly search engines.
- Tails is a mere 1.3 GB download, so on most connections it will download quickly.
- The key is to encrypt your traffic BEFORE you use Tor so that your ISP (Internet Service Provider) doesn’t see you’re in the Tor network.
- No one really knows the size of the dark web, but most estimates put it at around 5% of the total internet.
- It’s not that Tor is evil; it’s just that the same tools that protect political dissidents are pretty good at protecting criminals too.
Encrypted Messaging Apps And Private Communities
As I mentioned previously, using the Tor Browser will slow down your browsing. Since your traffic goes through a series of relays, getting encrypted or decrypted along the way, things slow way down. This means Tor is a lousy option for streaming video, online gaming, or downloading files (torrenting).

Risks Of Accessing The Dark Web:
If your Social Security number is found on the dark web, take immediate action to protect yourself. Additionally, contact the Social Security Administration to report the breach and discuss further protective measures. If you decide to venture into the dark depths of the deep web, make sure you’ve bolstered your device’s security with powerful privacy and security tools that can defend against dark web threats.

How To Get On The Dark Web Safely?
While there are other dark web browsers, they’re generally unreliable, unsafe, and complicated. The safest way to access the dark web on your phone is by using the official Tor Browser for Android or the Onion Browser for iPhone. That said, illegal actions remain illegal, whether on the dark web or not. Some regions ban the Tor network entirely, such as China, Russia, and Iran, so check your country’s laws before using it. A VPN also helps protect you from risks in the Tor network itself.

Navigating Dark Web Directories Safely
The dark web — sometimes called darknet — is a small portion of the internet that is hidden and can be accessed only by using specific software, configurations, or authorization. The dark web itself also has plenty of dark web site directories. However, it’s important to be cautious when navigating dark web directories like The Hidden Wiki, which is notorious for hosting low-quality or harmful links, including phishing scams. Always carefully scrutinize the URLs you visit, and never input personal information unless you know a site’s legitimacy. You might also consider using virtual machines (VMs) for an added layer of security. Tools like VirtualBox or VMware let you isolate your activity in a virtual OS.
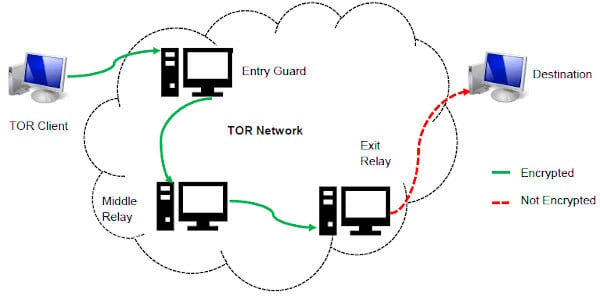
The main purpose of TOR is to provide access to the dark web and bypass censorship and surveillance in countries with restricted internet access. On the other hand, the TOR browser is a web browser that uses the TOR network to offer users private and anonymous internet browsing. Instead, use dedicated search engines, like DuckDuckGo (.onion version), Ahmia, Not Evil, or Torch.
To say that the dark web is a place of illegal activities only amounts to throwing the baby with the bath water. In fact, among the many features, it has unique options such as double VPN and Tor over VPN. Freenet allows connection to the darknet mode and the OpenNet mode. In darknet mode, Freenet will allow you to connect and share content with only your friends on the network. In the OpenNet mode, Freenet automatically assigns peers on the network. I2P aims at protecting communication monitoring by third parties and from dragnet surveillance.
- While they can’t see your browsing activity, some countries monitor or flag Tor users.
- This is because law enforcement often actively monitors these sites.
- Yes, if you don’t use a VPN, your ISP can see that you’re connecting to the Tor network.
- NordVPN works on every Tor-friendly system – Windows, Android, Linux, and macOS.
- We’ve also previously mentioned the “dark users” that use the dark web for illegal reasons, but the less said about them, the better.
- If you don’t use the right tools or settings, your ISP can still flag your connection.
These platforms are hubs for various services and goods, and understanding their features is key to navigating them safely. The first step is to download and configure the Tor browser from its official website. The Tor browser is your gateway to the dark web, allowing you to access .onion sites anonymously. The difference is the order in which your internet traffic travels.
Install A Virtual Private Network (VPN)
When using this method, Tor will encrypt your request, which will pass through your ISP unhindered. From there, it will go through a VPN server that conceals your IP and wipes geo-locations tags and other elements your Government or ISP might use to track the request. Choosing Tor over standard browsers is crucial for dark web navigation due to its unique privacy features.
In 2008, the Tor Browser was released, which made it easy for anyone to get on the darknet. The existence of an anonymous and hidden internet then allowed for alternative information channels and illegal websites to flourish. Some hackers offer ransomware as a service (RaaS), where cybercriminals can “rent” a strain of ransomware from its creator in exchange for a fee or a percentage of their ransom payments.
If you want to dive into the Dark Web using your smartphone, I’m here to debunk the myths and walk you through it step by step. Ready to start your undercover internet adventure on your Android or iPhone? Join millions of users who trust ForestVPN for privacy and unrestricted internet access. To maintain anonymity on the dark web, use strong passwords, avoid revealing personal information, and consider using a secondary device that doesn’t contain sensitive applications. Preventive Approach participates in various affiliate marketing programs, which means we may get paid commissions on editorially chosen products purchased through our links to retailer sites. On top of that, the provider offers perfect forward secrecy (PFS).
Pixel Privacy believes in digital privacy and does not believe in using it for heinous and/or illegal activities, and so the focus of this article will be on legal activities. Only access the dark web with both a VPN and the Tor Browser active. Avoid altering any security settings in Tor that could reduce your protection. Do not use any personally identifiable information on the dark web. Use aliases and avoid any activity that might reveal your identity. For advanced users, I2P offers configuration options for adjusting bandwidth limits, adding encryption layers, or even setting up your own eepsites.



