
If you’re in the U.S., you can make use of helpful tools like ExpressVPN’s Identity Defender to inform you if and when any of your data ends up on the dark web. This will allow you to take action right away and reduce the risk of any further damage to your data or identity. Let’s look at two popular browsers you can use to access the dark web on desktop computers and laptops. As a general rule, never download anything at all from the dark web. There are all sorts of threats on the dark web, and it’s all but impossible to verify whether a file is legitimate, so you’re likely to inadvertently download malware to your device.
Whonix OS: Advanced Security Through Isolation
- They can sometimes identify users through other methods, such as monitoring behavior, exploiting vulnerabilities or conducting undercover operations.
- If you’re on the dark web to engage in illegal activity and your traffic passes through a compromised exit node, your secrets can be exposed.
- Some consider VPN over Tor more secure because it maintains anonymity throughout the entire process (assuming you pay for your VPN anonymously).
- Most internet users access the deep web several times a day to perform common tasks, such as checking email, accessing a bank account, or reviewing health or school records.
- To provide anonymity, Tor is generally quite effective, but not completely foolproof.
- While not mandatory, using a VPN adds an extra layer of privacy and security by hiding Tor usage from your internet service provider.
(The installation instructions that follow are for the macOS platform, I’ll mention where it’s different for Windows.) Simply double-click the downloaded file in your download folder. Make sure that when you download the Tor file, it’s from their official website. The majority of the users on the dark web use the Tor (The Onion Router) browser. A vast number of URLs have domain endings such as “.onion”, which means that the URLs are only accessible by Tor users. Data gleaned from ransomware and data breaches is available on the dark web.
Start The Tor Browser
By disabling, you reduce such attacks’ potential (especially on untrusted websites). This guide reviews tools such as Tor, I2P, Whonix, and more for accessing the hidden web securely. Merely downloading, installing and using the Tor Browser is not illegal. This is why I strongly advise anyone visiting the dark web to exercise the greatest of caution during their dark online travels. Check out my article for more information about the dark web and how to access it while staying safe. One way to stay safe is to use a VPN while accessing the dark web, so be sure to check out my article on the best VPNs for the dark web.
Step 1: Download Hyphanet
The dark web continues to be a valuable tool and exchange network for many groups around the world. Some consider it an outright necessity, as it helps encourage free speech, maintain a free press, and support the work of law enforcement and government agencies. Victims accidentally download RAT when clicking on a website or any other link. However, I2P has several advantages, such as being more reliable and speedy than Tor. Also, its P2P routing design is more advanced and does not rely on a trustworthy directory to obtain route information.
(Optional) Change The Tor Exit Server
The NSA and other international espionage organizations cannot completely avoid the darknet. However, with the adoption of strict safety measures, practical anonymity can be attained. Instead of being targeted by sophisticated opponents, Tor and other darknets protect users from widespread surveillance. I2P, also known as the Invisible Internet Project, stands as a formidable darknet browser akin to Tor. It employs garlic routing and encryption, with dark web sites denoted by the .i2p suffix.
Keep in mind that in some regions like China and Russia, it’s illegal to use anonymizers. If you’re in a restrictive country, you’ll be crossing the red line and authorities could be at your heels. The silver lining is that no one has been arrested or prosecuted for using an anonymizing browser. Discovered pages are indexed in an extensive database and ranked based on numerous factors. When you search a term (or query) in a web browser, the search engine combs through the database to find relevant results and serves them up on SERPs.
The Tor Browser – What Is It?
With TOR installed, all you need to do is fire up the browser then head to a dark web domain. Since these aren’t indexed on search engines like Google or Bing, you’ll need to dig around subreddits like r/Tor or r/onions to find them. These resources are also packed with important tips to help you stay safe while navigating those dark waters. But with the NSA setting up fake exit nodes, and growing concerns about the overall security of the network, you may need a VPN as well, if you want to ensure your privacy.
Open The Tor Browser
However, though the dark web is synonymous with nefarious activity, it does have some benefits. We’ll also shed light on some of the legal uses of the dark web and show you how to access it securely in a detailed step-by-step guide. Ultimately, the dark web can be a place of great intrigue, but it’s essential to approach it responsibly. It is a realm that demands both mindfulness and education about the risks and ethical considerations involved. With the right knowledge and precautions, you can explore the dark web with enhanced privacy and security.
Is It Legal To Access The Dark Web?
Brave is easier to set up, though, and is already more privacy-oriented than most browsers. I2P offers several advantages over the Tor network, such as faster access to hidden services and support for BitTorrent, and it is generally harder to compromise. It is easier to install on Windows with the Easy Install Bundle (with all necessary components prepackaged).
Bypassing Content
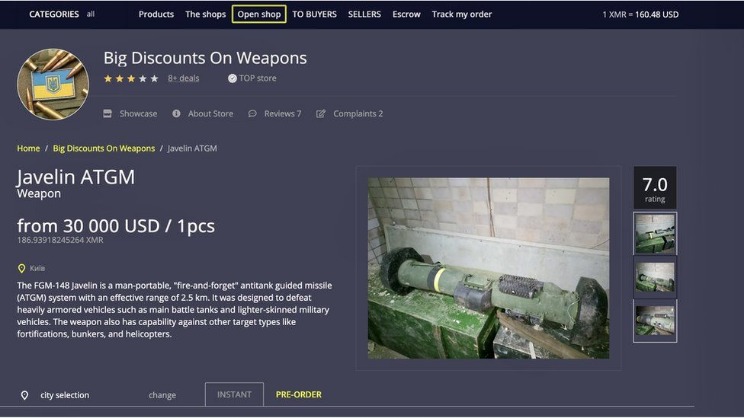
The attacks have led to the formation of other cybercriminal groups and Cyber Extortion. According to recent research, Bitcoin tumblers are increasingly used for money laundering. Fraudulent activities on the dark web include phishing scams, fake identity sales, and the sale of fake products.
Since their deadline wasn’t met for the closer of the sites a month later, the Impact team ascended to the dark web, where they started to publish the data. The child pornography site Playpen is one of the famous scenarios that resulted from the dark web. The site had only been up and running for about seven months, but surprisingly, it gained over 215,000 users.

Phishing attempts remain common, tricking users into revealing personal details, login credentials, cryptocurrency wallets, or financial information through deceptive websites and messages. In 2025, each of these browsers presents unique strengths and limitations. Selecting the optimal tool depends primarily on your individual privacy requirements, technical expertise, and the specific contexts in which you plan to access the dark web. Install AVG Secure VPN to encrypt your internet connection and protect your privacy wherever you go on the web. Download AVG Secure VPN to encrypt your internet connection and protect your privacy wherever you go on the web. Law enforcement officials are getting better at finding and prosecuting owners of sites that sell illicit goods and services.
The 2024 Global Threat Report unveils an alarming rise in covert activity and a cyber threat landscape dominated by stealth. Data theft, cloud breaches, and malware-free attacks are on the rise. Read about how adversaries continue to adapt despite advancements in detection technology.

Exploring the dark web can be a fascinating journey, but it requires the right tools and safety precautions. From popular options like Tor to specialized environments like Whonix and Tails, each dark web browser offers unique features to enhance your privacy and security. Navigating the dark web responsibly and cautiously will help ensure your experience remains secure. Always prioritize safety and legality, and remember that your actions on the dark web can have real-world consequences. It also adds an extra layer of anonymity, which is particularly important when browsing the dark web.
When using Tor Browser, it is important to note that while it provides a higher level of anonymity, it does not guarantee complete protection. It is still possible for malicious actors to monitor online activities, especially if users engage in unsafe browsing practices or download suspicious files. The Tor Browser provides anonymity and privacy by routing your internet connection through a network of volunteer-operated servers around the world. This process, known as “onion routing,” masks your IP address and encrypts your data, making it difficult for anyone to trace your online activity. The dark web is a subset of the deep web, which includes any online content not visible on normal search engines, such as private databases and personal email accounts.



