
These sites are only accessible over the Tor network and are commonly used for privacy and anonymity. The Tor Browser also features many built-in protections that protect against tracking and fingerprinting. They can monitor exit nodes but cannot easily trace traffic back to individual users unless mistakes are made.
Proton VPN
- To access the Dark Web, users need to use a specialized browser, such as the Tor Browser, which connects and communicates with the Tor network.
- The dark web is not meant for the general public since it is harder to access and need technical knowledge.
- The Dark Web remains a shrouded corner of the internet—an enigmatic space where privacy, free speech, criminality, and censorship resistance intersect.
- Simply download the file, install the software, and you’re ready to use its web-based interface.
- To access the dark web, you need an anonymizing web browser or any browser that supports the Tor network.
These are only a few of the .onion search engines that are available. The exit node removes the final layer of encryption on your data. While this doesn’t tell the exit node what your original IP address or your geographical location is, it could spy on your activity if the website you’re visiting isn’t a secured HTTPS website. As digital landscapes evolve, so do the methods of accessing hidden content and maintaining anonymity. By following these steps, you enter the Dark Web with more confidence and preparedness. Although it’s not inherently illegal to access the Dark Web, remember that certain sites and activities may be.
Advantages Of Tor Over VPN
We don’t want to leave you with the impression that everything on the dark web is nefarious or illegal. The Tor network began as an anonymous communications channel, and it still serves a valuable purpose in helping people communicate in environments that are hostile to free speech. “A lot of people use it in countries where there’s eavesdropping or where internet access is criminalized,” Tiquet said. The terms “deep web” and “dark web” are sometimes used interchangeably, but they are not the same. Deep web refers to anything on the internet that is not indexed by and, therefore, accessible via a search engine like Google.
Hacking Services And Groups
Afterwards, your request will be matched with the appropriate website. Tricky, but effective; that’s why it’s, by far, the best method to access dark web content. Privacy and anonymity are the dark web’s hallmarks, thanks to a network of servers that hide users’ identities and locations.
How To Access The Dark Web On Your Device
Apart from his professional endeavors, Samson is passionate about soccer and enjoys reading, table tennis and watching sports in his spare time. He has also contributed to platforms like Financesonline.com and Timeero.com. Although the dark web is a small portion of the internet, experts estimate it to account for 5% of all internet content (Spiceworks, 2025)2. According to McAfee, the deep web is about 10 to 20 times larger than the surface web, making up 90 to 96% of the internet3. On iOS, the recommended option is Onion Browser, but due to Apple’s restrictions, it lacks full Tor functionality. To improve security on mobile, you should always use a smartphone VPN, disabling JavaScript, and avoiding sensitive activities on mobile.
- This article will explore the legality of the dark web, how it works, and what you need to know before accessing it.
- No one really knows the size of the dark web, but most estimates put it at around 5% of the total internet.
- As a result, you should avoid opening unfiltered sources, torrent sites, and dark web links unnecessarily and downloading every file you come across.
- If found, take immediate steps to secure your accounts and personal information.
- I don’t recommend seeking out dark web content unless you have a specific reason to do so.
Install Antivirus Software

I2P is an anonymous overlay network designed primarily for peer-to-peer applications. The dark web is a part of the internet that isn’t indexed by search engines. You’ve no doubt heard talk of the “dark web” as a hotbed of criminal activity — and it is.
Platforms like SecureDrop provide a safe space to communicate and share information anonymously. The anonymity surrounding Dark Web makes it both intriguing and controversial since people argue about its ethical and legal boundaries. Government authorities and cyber security professionals continuously observe this untraceable domain to detect and report cyber offences.
Use A Trusted VPN
It has been estimated that a large percentage of dark web traffic is related to illegal pornography that includes underage victims. Tor relays are servers run by volunteers, designed to keep your activities private and untraceable. A VPN hides your internet activity, making it harder for your connection requests to be traced back to you. It’s a precaution to protect yourself before diving into the dark web. For recommendations on choosing a VPN, look for expert reviews and articles.
Features Of The Dark Web

Still, there are plenty of good reasons to access it, like research, whistleblowing, journalism, and financial privacy. Cybercrime services, such as hacking tools and stolen databases, are available for hire, creating a marketplace for illicit online activities. Dark web monitoring platforms provide secure communication channels for individuals seeking to expose information without fear of retribution. Additionally, the Dark Web serves as a haven for those in censored environments, offering access to restricted information and enabling the free expression of opinions. Proton VPN makes it easy to safely gain access to the dark web by connecting users to the Tor Network in a single click. Its server network includes dedicated nodes set up to reroute internet traffic through the Tor network.
All Tor Browser data is encrypted and relayed three times over the Onion Router network, which is composed of thousands of volunteer-run servers, which are known as Tor relays. The dark web is just misinterpreted; it is not intrinsically dangerous. Used ethically, such as for privacy or study, one can search this area lawfully and safely. Combined with smart surfing behaviour and technologies like Tor and a VPN, even the darkest reaches of the internet may be securely traversed. Only access the dark web with both a VPN and the Tor Browser active.
If your Social Security number is found on the dark web, take immediate action to protect yourself. Additionally, contact the Social Security Administration to report the breach and discuss further protective measures. Install Norton 360 Deluxe to help secure your device, block scams, and stay private online. Download Norton 360 Deluxe to help secure your device, block scams, and stay private online. Get Avast BreachGuard for Mac to protect your privacy and keep your personal data from falling into the wrong hands.
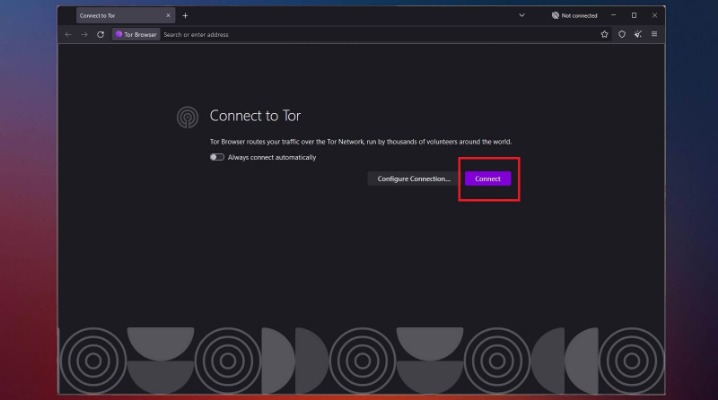
Though you likely won’t remember the addresses of onion websites, you can find these URLs on various websites on the internet. Check onion links through trusted directories, user reviews, and reputation checks. Use directories like The Hidden Wiki or Dark.fail, which list verified and regularly updated onion links. Install Tor Browser from the official website, adjust security settings to “Safer” or “Safest,” and only use trusted onion links from verified directories. For journalists, students, researchers, and security professionals, it’s a powerful tool when used ethically and safely.
SecMail is one of the most popular email services on the dark web. While this is not much compared to standard email services, it is enough for PGP-encrypted messages. ProtonMail is a Swiss-based email service that is very easy to use. You are not required to provide your personal information to create an account.



