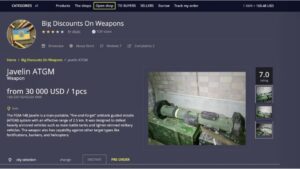
Transactions are streamlined through cryptocurrencies, primarily Bitcoin and Monero, ensuring fast and anonymous payments. Escrow systems and...
Uncategorized
Believe it or not, some dark web marketplaces have pretty advanced systems for building trust. Sellers often...
Though people usually think of dark websites as the wrong online place, that’s not the complete truth....
Caches of drugs are hidden under park benches, rocks, holes in walls, buried under dirt or snow,...
To counter this, dark web monitoring has become essential to detect these threats and safeguard digital privacy....
“Operation RapTor shows that the dark web is not beyond the reach of law enforcement,” said Head...
Dream market url reddit Tight now only Dream market is deserving on the top spots in the...
You can archive any site you want, or retrieve historical records wherever available. Monero’s privacy beats Bitcoin’s...
These markets also prioritize user feedback and reviews, allowing buyers to make informed decisions based on the...
It is one of the most active and up to date markets and always provides new and...