Despite multiple takedown efforts by law enforcement and security researchers, Brian’s Club has resurfaced repeatedly and continues to add new stolen credit card data. The dark web market changes all the time, but some dark web marketplaces have made a name for themselves as the biggest and busiest spots. These sites attract thousands of users every day, offering all kinds of illegal goods that keep the underground trade going. It’s a bit of a contradiction to talk about search engines for dark web sites because, by definition, these are not sites that get indexed by traditional search engines. Many dark web search engines on the darknet suffer from spam, because these spammy sites want to be indexed and found by the search engines as opposed to genuine onion sites.
Encrypted Communication Tools
KeyBase combines encrypted messaging with secure file sharing and identity verification. Its dark web version provides the same functionality as the clear web option, while adding Tor’s anonymity layer. SecureDrop stands out as the leading platform for secure document sharing used by major news organizations.
- It aims to preserve the internet’s scientific and cultural heritage.
- However, when it comes to darknet markets, the story is very different.
- By supplying stolen data, these dark web links fuel many online scams and identity theft operations, playing a critical role in the darker aspects of the internet.
- The cybersecurity challenges seen in 2024 highlight the dynamic and ever-evolving nature of cyber threats.
- Since Hidden Wiki maintains all kinds of websites, ensure you don’t open something you don’t want to see.
- Once you signup, you can check pricing info, available products and vendor details.
Keep Tor Browser Updated
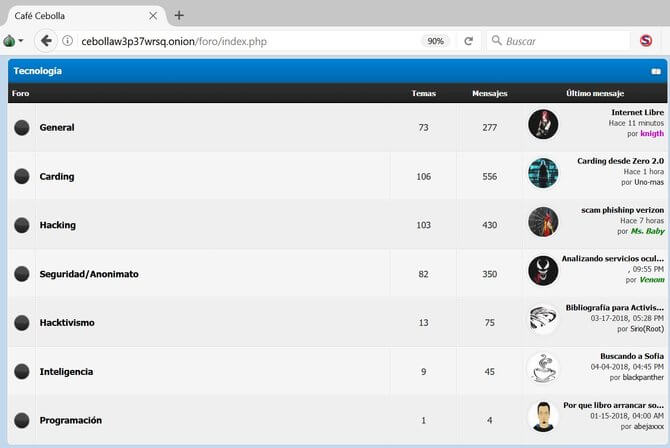
In this post, we’ll walk you through the top 10 dark web marketplaces that you need to watch for potential threats to your organization. Deep web websites have to be hosted somewhere, and Impreza Hosting is one of those anonymous dark web hosting services. A host is basically a website’s house, or where it lives and takes up space.

Onionname
- Some might say that Russia currently has more dark-net markets than ever.
- Even people with little to no knowledge can buy ready-made ransomware and launch attacks on their victims.
- Future work may further extend the approach presented here, for example using machine learning methods to capture further behavioral regularities.
- Since the ISP can’t detect you’re accessing dark web URLs, it won’t trigger any alarms about your online activity.
- The website’s articles focus on digital rights, surveillance, and security research.
The White House market offers impressive features like a mandatory PGP requirement that enables 2FA for the user’s profile and adds a protective layer. It’s a user-only marketplace, meaning you need to register to enter. During our tests for the research, we were able to register with a bogus email and a random username. The market doesn’t verify email and has good security in place. All that one can expect from a deep web marketplace when it comes to anonymity and security. The browser uses onion routing technology to route the internet traffic through multiple relay nodes that provide layered encryption.
Safe Dark Web Links To Explore
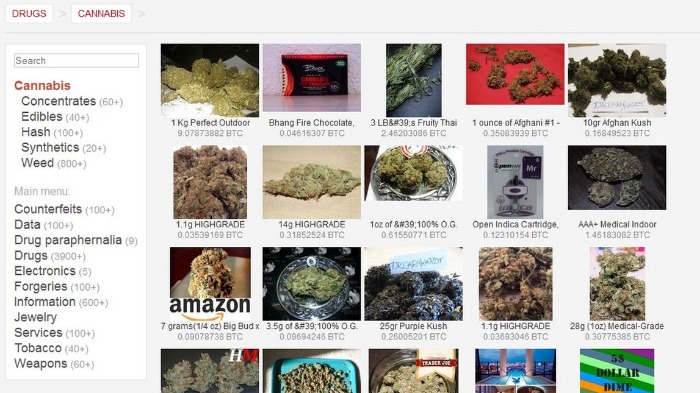
And (c) is the dark web, which is the part of the deep web that isn’t indexed by search engines and requires special tools like Tor Browser to access. Riseup is a volunteer-run social movement organization that offers email, email lists, a VPN, online chat, and other online services for political activists engaged in various causes. Riseup’s services can be accessed on the surface web or via Tor websites if users want to protect their anonymity.
Nevertheless, due to their unregulated nature, DWMs exhibit behaviours not observed in regulated marketplaces. They offer anonymity to their users by using and developing specialized tools. DWMs are accessed through darknet browsers supporting the onion routing protocol (e.g., Tor), which provides anonymous communication connections35. Additionally, transactions are made with cryptocurrencies, mostly Bitcoin, which also provide anonymity to the transaction parties6,36.
If you wish to access the snapshots of these websites, just type in the domain name, and you will get the results depending on how many records exist on the website. This platform is a time capsule with content, primarily web pages. It saves a select version of each page and preserves it even after upgrades have taken effect on the original site. The Comic Book Library is the home for all your comic book needs.
Bonus: The Silk Road

Onion sites are considered part of the deep web because search engines like Google and Bing can’t index them. City Market is a modern darknet hub designed to emulate the flow and structure of a digital metropolis. With intuitive navigation, categorized listings, and responsive support, City Market offers a smooth experience for users at any level. Its blend of simplicity, speed, and secure transactions makes it a reliable choice in the evolving darknet space. Unlike other search engines, it does not collect or share web activities and personal data of users.
How Do I Use A VPN With Tor?
Then, after operation Bayonet, the number of sellers in all categories and multisellers significantly drops, as shown in Fig. Notably, the number of multisellers suffers the largest drop of \(-99\%\) by the end of the first quarter of 2018. The cybersecurity challenges seen in 2024 highlight the dynamic and ever-evolving nature of cyber threats. As cryptors, loaders, and stealers become more sophisticated, and underground markets remain resilient, organizations must prioritize robust cybersecurity measures in 2025. Contrary to predictions, the market for cryptocurrency “cleaning” services, or Bitcoin mixers, stagnated.
Although these marketplaces are continuously shut down by law enforcement agencies, they still work today. Interestingly, new sites get more hype, and it even becomes difficult to shut them down, as they have better security than the older ones. Despite growing crackdowns from law enforcement agencies, the dark web remains a hotbed of criminal activity, offering everything from drugs to stolen data. We showed that a small fraction of traders is responsible for a large fraction of the trading volume, and by analysing the networks of buyers and sellers, we found different resilience regimes. Shocks tend to induce serious structural changes in the multiseller network, but impact the multibuyer network much less severely.
But no matter how polished or professional these sites seem, the risk of getting scammed — or tracked — is always high. Most buyers and sellers use the Tor network, which hides IP addresses and locations. Doing so makes it harder for authorities to identify who’s behind a purchase or a listing. Vendors often build up reputations through ratings and reviews, just like sellers on mainstream platforms. To reduce scams, many markets also use escrow systems, where the site holds the buyer’s payment until they confirm the item has been delivered.

Many dark net sites do not undertake the necessary measures to protect users like most websites on the surface web. As a result, you can be exposed to different malware types, including botnets, ransomware, keyloggers, and phishing. All in all, it is not illegal to access the dark web, but it can create issues for you. If you don’t take the necessary measures, many unsavory activities can expose you to unnecessary risks. With rising online privacy concerns in the current digital age, the Tor network’s anonymity is becoming essential.
Tor And The Onion Browser
Activists and government critics prefer to remain anonymous, fearing repercussions if their identities are revealed. Besides, victims of crime may want to hide their identities from their perpetrators. Nonetheless, if whatever you do is deemed illegal in your country, you can get into trouble. The use of the dark web raises suspicion as it shows there is something you want to do privately. Remember that illegal activities can still incriminate you, whether you are using a Tor browser. For example, you shouldn’t pirate copyrighted material, engage in terrorism, or share illegal pornography.



