The accessibility of Tor has helped it evolve into a multifaceted ecosystem with both positive and negative uses. Each time the authorities take down a darknet market, it leads to a string of high-profile arrests. Yet each time, another string of darknet markets pop up to hoover up the users and continue working. The most extreme forms of illicit content are locked in private forums. But you should not go looking for things you do not want to find the answer for.
Dark Web Monitoring Solutions: Detecting Threats Before They Happen
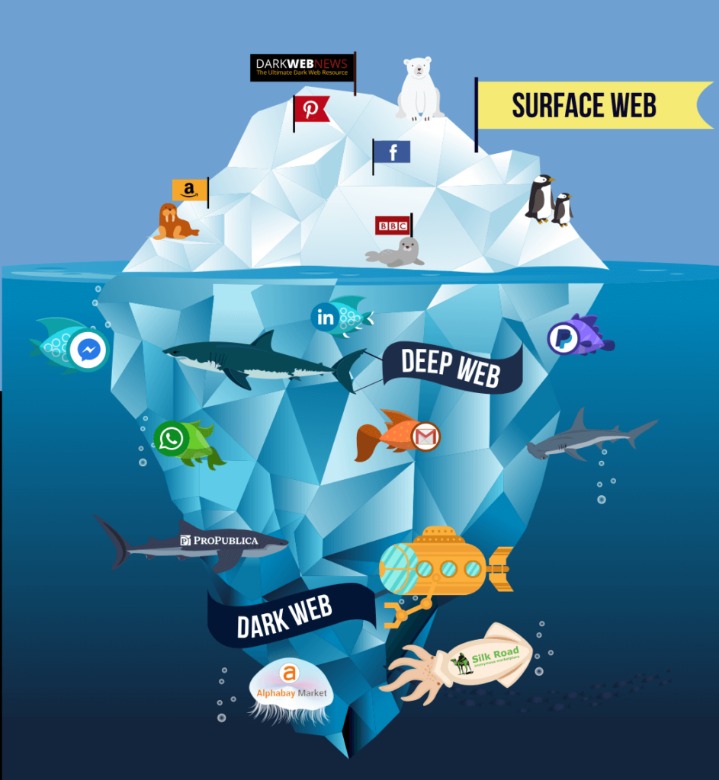
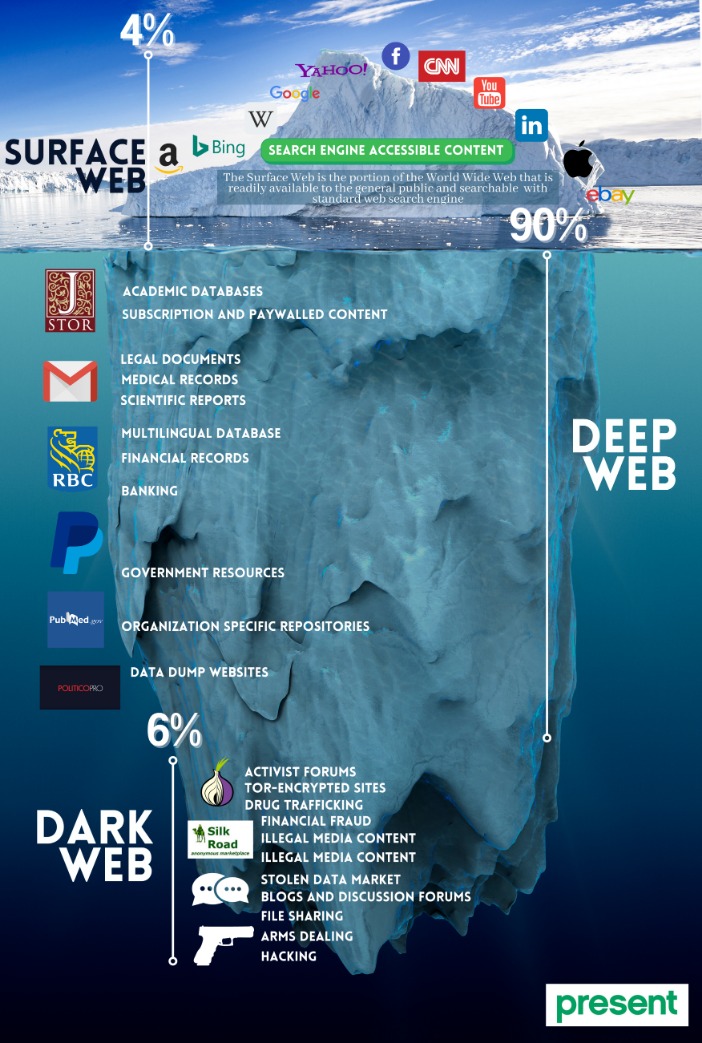
Deep web sites may be concealed behind passwords or other security walls, while others simply tell search engines to not “crawl” them. Without visible links, these pages are more hidden for various reasons. In the U.S., dark web usage has been growing steadily—not just among cybercriminals, but also among privacy-conscious users.
Related Articles From The Safe Browsing Section
However, new technology like encryption and the anonymization browser software, Tor, now makes it possible for anyone to dive dark if they’re interested. At the dark end of the web, you’ll find the more hazardous content and activity. Tor websites are located at this far end of the deep web, which are deemed the “dark web” and are only accessible by an anonymous browser. Locating surface web websites is possible because search engines can index the web via visible links (a process called “crawling” due to the search engine traveling the web like a spider).
Hacking Services And Groups
Hackers sell access to email accounts, social media profiles, or other information that can be used for identity theft. The Hidden Wiki is a surface website offering a collection of dark web links. Before visiting any dark websites, get comprehensive cybersecurity software to help protect yourself from threats you may encounter. Dark web browsing is not as simple as regular web surfing, but there are some tools you can use to chart your journey. Dark web search engines and forums like Reddit can help you find reliable dark websites, and you’ll need to use a dark web browser to visit them. The dark web refers to content on the internet that is intentionally hidden and requires special software like Tor Browser to access.
Dangers Of The Dark Web
- The dark web is also unregulated, meaning that it is run and upheld by a vast network of individuals around the world.
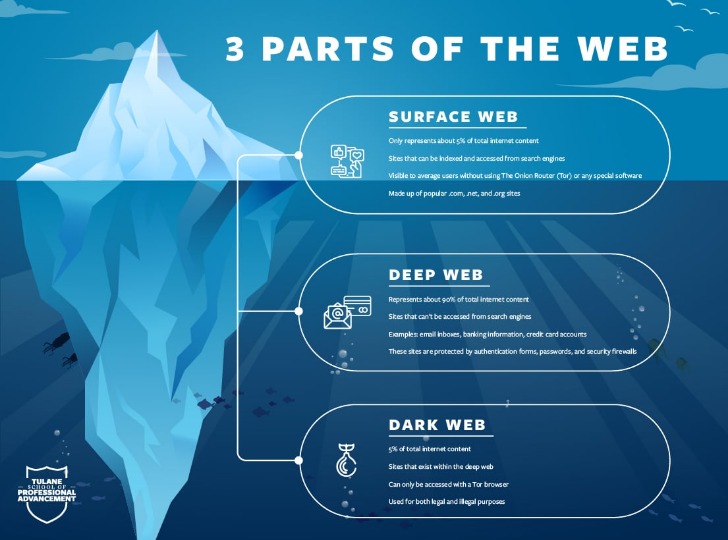
- The dark web is a part of the internet not indexed by standard search engines like Google or Bing.
- There’s no such thing as perfectly private or secure on the internet.
- Some alleged services like the professional “hitmen” may just be scams designed to profit from willing customers.
- Deep web refers to anything on the internet that is not indexed by and, therefore, accessible via a search engine like Google.
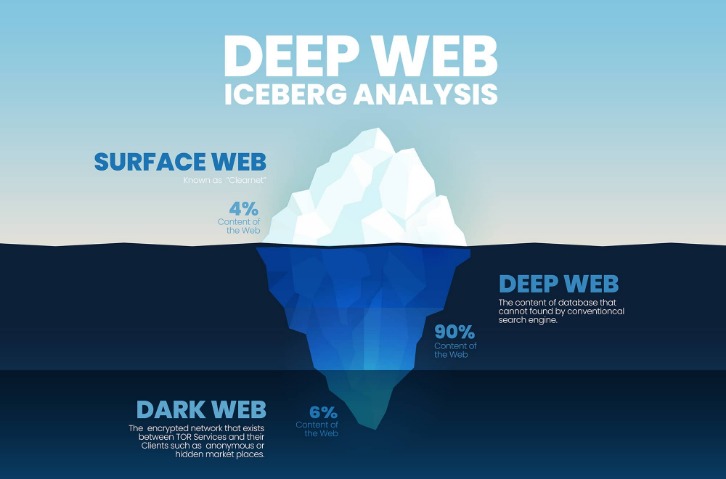
But broadly speaking, the web can be divided into 3 main parts which are Surface Web, Deep Web and Dark Web. Download Tor Browser to experience real private browsing without tracking, surveillance, or censorship. Tor Browser aims to make all users look the same, making it difficult for you to be fingerprinted based on your browser and device information. Cryptocurrency is often used for payments on the dark web, exposing users to fraud or money laundering schemes. Malware, ransomware, and hacking tools are widely sold in underground forums.
How To Get On The Dark Web: A Step-by-Step Guide
As cyber threats grow more sophisticated, organizations are keeping a close watch on the dark web. Companies use dark web monitoring to scan for leaked data, stolen credentials and breach indicators, helping them track and identify perpetrators. But let’s be realistic, the best defence isn’t just playing detective after the fact. It’s making sure your sensitive information never lands there in the first place. Their addresses are often a jumbled mess of letters and numbers, almost impossible to remember, like the notorious “eajwlvm3z2lcca76.onion”, which once served as the gateway to the infamous Dream Market. The dark web didn’t start as a haven for cybercriminals – it was actually developed for a very different purpose.
Types Of Threats Associated With The Dark Web
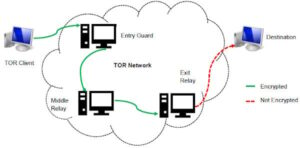
Certain details of your traffic can be intercepted at the entry and exit points of the node, by the people running those nodes, if they know what they’re doing and what they’re looking for. You’re also open to threats like end-to-end correlation attacks, so while Tor is a lot more secure and private, it’s by no means completely safe. The dark web comes with its own set of tools and services, including web browsers and search engines (which I’ll get on to in a moment). Part of what makes the dark web the dark web is that you can’t access it through your normal web browser, nor can you look something up on it via a Google search. In this volatile ecosystem, recognizing the dynamic nature of the dark web is half the battle.
And all the Dark Web sites have weird domain addresses and end in .onion suffix so that they are much harder to track and only accessible by Tor. Tor routes your internet traffic through a global network of volunteer-operated servers, hiding your location and encrypting your data at multiple levels. This makes it nearly impossible for anyone—governments, internet providers, or hackers—to trace your browsing activity back to you. While the Tor Browser looks and feels similar to Firefox, it’s specifically designed to connect to websites that aren’t accessible via regular browsers. Understanding its dual-use nature is essential for navigating its risks and leveraging its benefits responsibly.
Malware, ransomware, and hacking tools are also readily available for purchase or rent, enabling attackers to launch sophisticated campaigns. Additionally, forums facilitate the exchange of exploit kits and zero-day vulnerabilities, which can be weaponized before patches are released. The anonymity of the dark web makes it a fertile ground for coordinating cyberattacks and sharing illicit services without detection. The dark web can be dangerous due to the presence of scams, cybercriminals, and malware. Users should exercise caution and follow safety practices to minimize risks. For many of us, the dark web represents an enigmatic corner of the internet, often shrouded in myth and misunderstanding.
Secure Your System And Mental Well-being
- Examples include SecureDrop and GlobaLeaks, which are used by journalists and activists to securely receive documents and tips.
- The most common darknet software is the free and open-source Tor, short for the Onion Router.
- Great life advice, but it’s even more valuable where the darknet is concerned.
- Many sites become defunct quickly, either because they are shut down due to illegal activity, their founders lose interest, or they change addresses and names to avoid detection.
I2P can only be used to access hidden sites that are only available on the I2P network. As I mentioned previously, the dark web is quite popular with journalists, political bloggers and news publishers, and others who run the risk of imprisonment in countries like Iran and others. Supreme Court will allow the FBI to search and seize any computer that’s using the Tor browser or VPN.

People also use it for illegal purposes, including buying and selling drugs and weapons, along with other highly unsavory activities. DuckDuckGo runs on the Tor network and lets you search any part of the internet without tracking or storing your data. It offers standard features like image, video, and news searches, but also includes tools like anonymous chat, AI search results, and secure browsing. The Dark Web Hub equips law enforcement, enterprises, MSSPs, and researchers with essential knowledge to navigate dark web threats. Despite what the name implies, it isn’t illegal to access the dark web.
Data brokers such as LocalBlox for instance crawl the web and store information about business and consumers to sell for marketing purposes. Most corporate and public sites work hard to make sure that these web crawlers can easily find them. This makes perfect sense as the entire purpose of creating a website is so that people can access your content and/or buy your products. Most sites do this by deliberately placing “meta tags” in their website code to make it easier for crawlers to catalog them properly. Browsers such as Google, Bing, DuckDuckGo act like virtual librarians, sorting and cataloging materials so they can be easily searched. They do this through using “crawlers”, sometimes also known as “spiders” or “robots”.