
Moreover, the layers of encryption and the bounce of your data from node to node effectively mask your IP address, enabling online anonymity. It allows access to the .onion sites on the dark web that you won’t find using a regular browser. Despite being illegal, vendor credibility is essential in Dark Web markets. Sellers establish trust through a rating system, similar to legitimate e-commerce platforms, where buyers leave feedback on product quality, delivery speed, and communication. Some vendors offer “stealth shipping” guarantees, ensuring products are discreetly packaged to avoid detection.
Methods To Access The Black Market: A Brief Look
Darknet markets operate within this hidden space, often hosting illegal activity, while the deep web primarily consists of everyday private or password-protected content. Even if you’ve never visited these markets, your personal and financial data might already be there, having been leaked through a data breach. Criminals use this information for money laundering, opening bank accounts, applying for loans, and draining your finances. Many listings involve stolen personal information, including credit card data, Social Security details, and full identity profiles. In this article, we’ll explore what dark web markets are, how they work, and why they’re so risky.
- The Colonial Pipeline attack in 2021 demonstrated how a compromised password obtained from a Dark Web forum can result in millions of dollars in damages and widespread operational disruption.
- If you’re lucky enough, you can find it on clearnet privacy forums.
- To reduce the risk of fraud, many dark markets offer escrow services.
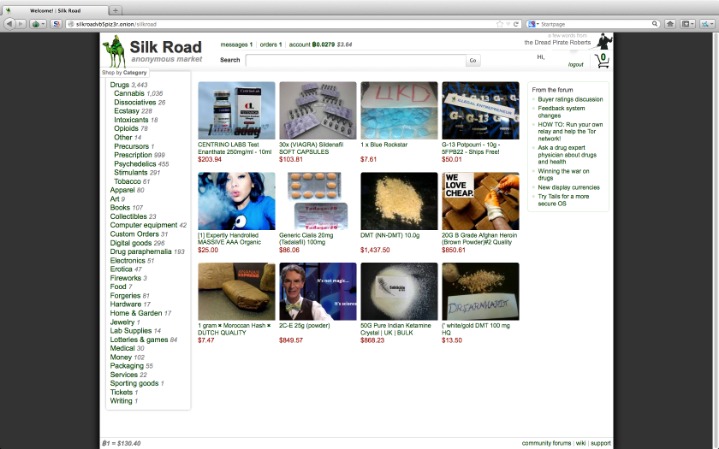
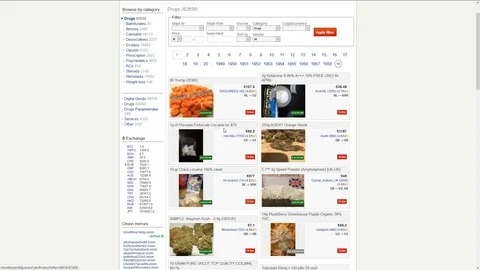
- However, the goods and services offered include stolen credentials, hacking tools, counterfeit documents, drugs, and weapons.
- A VPN hides your internet activity, making it harder for your connection requests to be traced back to you.
What Are Onion Sites And Dark Web Websites?
The advantages of I2P are based on a much faster and more reliable network. Additionally, I2P doesn’t rely on hidden directories that serve as a resource for .onion domains. I2P can only be used to access hidden sites that are only available on the I2P network. The majority of the users on the dark web use the Tor (The Onion Router) browser. A vast number of URLs have domain endings such as “.onion”, which means that the URLs are only accessible by Tor users. Hacker services against banks and other financial institutions are offered there.
Leverage Free Cybersecurity Resources
Moreover, the company also uses HTTPS and SSL encryption on the Onion site for extra protection. This makes it even harder for third parties to see your email traffic. ProtonMail is a Swiss-based email service that is very easy to use. You are not required to provide your personal information to create an account. The email service is available both on the surface and on the dark web.
Dark Web Black Market Technologies And Tools
Of course, not all activity on the dark web is criminal, but such marketplaces are where a lot of illegal trade and money laundering happens. By relying on encryption, pseudo-anonymous currencies, and network-level anonymity, they create a false sense of safety, drawing in both buyers and sellers. Data breaches like the ones mentioned above highlight the significant threats posed by dark web black markets. Stolen data can quickly transition from legitimate systems to underground forums, where it becomes a valuable commodity for cybercriminals.
Key Cyber Threats Facing The Financial Sector In 2025
We have simplified the cybersecurity assessment process and made it accessible for all businesses. One of the biggest problems cybersecurity teams face isn’t a lack of tools — it’s too many alerts. While this topic may seem distant for most people, understanding how these spaces operate is crucial. It helps us stay more vigilant, better protect ourselves, and make informed decisions online. In the first arc of the anime series Lupin the 3rd Part V, Lupin III steals digital currency from the “Marco Polo” darknet market. For a local machine configuration, he recommends a computer purchased for cash running Linux, using a local Tor transparent proxy.
BBC Tor Mirror

Onion sites use The Onion Router (Tor) software to encrypt their connections and enable anonymous communication. The dark web is the unregulated part of the deep web, which encompasses all parts of the web not indexed by search engines. While the deep web comprises about 90% of the total web, the dark web makes up just a tiny fraction of the deep web total. For cryptocurrency enthusiasts, Wasabi Wallet is considered an indispensable trading tool and one of the safest ways to buy, sell, and manage cryptocurrency on the dark web. Wasabi Wallet isn’t free to use, but, for a small fee, you get reliable and anonymous cryptocurrency transactions. It hosted over 7,000 .onion categorized links to make surfing the web easier.

Tweak Tor Browser Settings
Most e-commerce providers offer some kind of escrow service that keeps customer funds on hold until the product has been delivered. However, in the event of a dispute don’t expect service with a smile. Every communication is encrypted, so even the simplest transaction requires a PGP key. Dark web search engines exist, but even the best are challenged to keep up with the constantly shifting landscape. The experience is reminiscent of searching the web in the late 1990s. Even one of the best search engines, called Grams, returns results that are repetitive and often irrelevant to the query.
The dark web is a small segment of the deep web, which encompasses all parts of the internet not indexed by standard search engines like Google. Accessing it requires special software, such as the Tor browser, which provides anonymity by routing your connection through multiple servers. The black market, with its myriad links and hidden pathways, doesn’t have to be a forbidden zone. With the right tools, like Forest VPN, and a little know-how, it can be explored safely and legally.
The good news is that the platform will not see what you copy/paste. Your data is encrypted in the Tor browser before reaching the ZeroBin servers. This is the best place to get short and reliable links to an unalterable record of any webpage across government and corporate websites. Unfortunately, it requires you to have an invitation code to create an account.
Should I Only Use A VPN To Access The Dark Web?
This enables individuals to form groups and only share content in a highly anonymous network of darknet users who they know. From this point onwards, you can enjoy complete anonymity and security while being able to access “.onion” websites and other dark web browser domains. When you install a VPN, all of your activities on the dark web will be hidden from unwanted snoops from your ISP or the FBI.
Illegal Pornography
In fact, some parts of it actually provide a safe space for privacy and freedom, especially where traditional internet access is limited or censored. Even passive activity on these sites can contribute to criminal networks. For instance, buying fake documents may indirectly support larger operations involving trafficking, extortion, or organized crime. The exposed data included customer names, addresses, and purchase details.

Conspicuously absent are some preferred features, such as the lack of pre-order (direct pay) purchases, a multi-sig option for BTC payments, and forced PGP encryption for communications. It makes up for this with enhanced security and user safety features, helping users to ensure they are not getting phished. DarkFox Market is the largest dark web shop selling various products and attracting more vendors and users.
Its key features include kernel hardening, application firewall, package security, filesystem encryption, meta-proxy encryption, and binary integrity. The creators assert that because their technique is so strong, even malware with root access could not determine the machine’s IP address. Another essential security feature is that all incoming and outgoing data from the app is encrypted, including any private and public keys involved. Initially, the dark web was mainly used by government agencies, big businesses, hackers, and cybercriminals.



