That breach, caused by an attack that compromised POS (point-of-sale) devices, went undetected for nine months. The breach affected 860 convenience stores – 600 of those were also gas stations. PureVPN uses 256-bit AES encryption to ensure safety even when connected to a public WiFi network. The pausing/closing feature is especially useful if a specific Privacy Card has been exposed in a data breach or you want to block hidden/unwanted subscription charges. Keep in mind that you still need to reach out to the subscription provider if you’d like to cancel the service. We have compiled the zip codes of all cards for which it was available, and used the data for the following; let’s look at where the cardholders are located.
Card checkers are tools used by threat actors to verify the validity and authenticity of credit card information they purchase on the dark web. If your PayPal account or credit card details end up on the dark web, it’s essential to act quickly to minimize potential damage. Lastly, remember that the traditional web offers countless legitimate ways to engage in online transactions and protect personal information. Explore trusted websites and platforms that prioritize cybersecurity, privacy, and legal compliance.
How Can I Protect My Credit Card Info?
There are very few reports of this scam, but it could grow as RFID becomes more common. In this guide, we’ll explain how people steal credit card numbers, what they can do with them, and how to protect yourself now and in the future. Dumps have negligible value and risk, while the Fullz credit cards’ dark web value and, therefore, the risk is the highest. Some fake sellers take your crypto and never ship what you ordered, or phishing sites that look like real marketplaces but steal your login info.
Choosing a VPN provider with a successful track record of protecting user security and privacy would also be best. Some credit cards also include built-in fraud protection, which you can avail of to ensure your financial safety at all times. The stolen data reportedly includes a mix of credit and debit cards from major providers like Visa, MasterCard, American Express, and JCB.
Dark Web Credit Card Numbers: Understanding The Risks And Fraud
These measures include implementing robust security practices, such as encryption and multi-factor authentication, to protect credit card data and reduce the likelihood of it ending up on the dark web. It is crucial to approach the Dark Web with caution and fully understand the risks involved. It is illegal and unethical to engage in activities that exploit stolen credit card information.
Frequently Asked Questions About Dark Web Credit Cards
As a trusted platform for money management, credit education, and identity protection, our mission is to bring Financial Power to All™. Surfing on the dark web, communicating, or transferring private information is legal. However, buying credit card information from the dark web is illegal and leads to severe penalties from the government. Humans, being the slaves of habit, are more inclined to use the same kinds of passwords for most of their accounts.

Understanding Credit Card Fraud On The Dark Web
“The most important thing is for people to keep an eye on their transactions and report any fraud immediately,” Krebs says. Unless you live the rest of your life only paying with cash, you’ll never be totally impervious to payment fraud. Some fullz even include photos or scans of identification cards, such as a passport or driver’s license. This extra layer of security gives peace of mind in today’s digital world.
Stay In Control—Use Privacy Virtual Cards To Mask Your Card Details
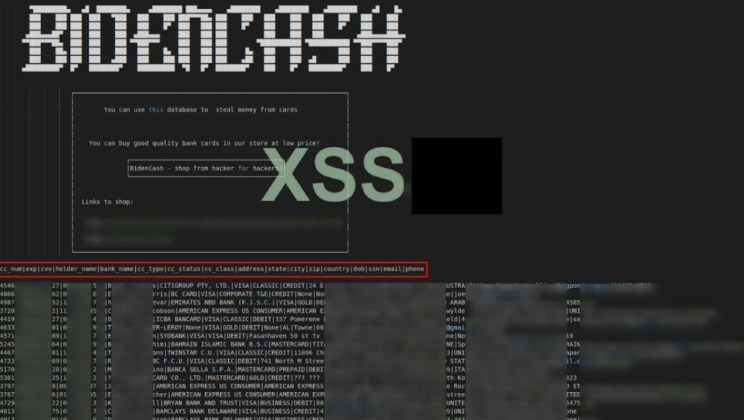
The first step you should take is to contact your bank or credit card issuer immediately. Inform them that your card information has been compromised and discuss the best course of action, which could include canceling the compromised card and issuing a new one to prevent fraudulent transactions. Active for a decade since 2014, it is a widely used credit card shop used to source stolen credit card information such as dumps, CVVs, Wholesale Accounts.
Credit Cards Skimmed And Used As Marketing Tool
The process, also called skimming, allows them to make physical purchases at ATMs or retail stores. Unlike online fraud, this type of theft is harder to detect because the transaction appears as a regular swipe. It is understood that the data included such highly sensitive information as the primary account number of the credit cards concerned, along with expiration dates and the card verification value, CVV2, security code. But that’s not all; there are also cardholder details such as their full name, address, date of birth and telephone number as well as email address. Pretty much everything you would need to commit credit card fraud or launch phishing attacks against the cardholder. In the past year, the dark web data market grew larger in total volume and product variety, so as supply grew, most prices plummeted, according to Zoltan.
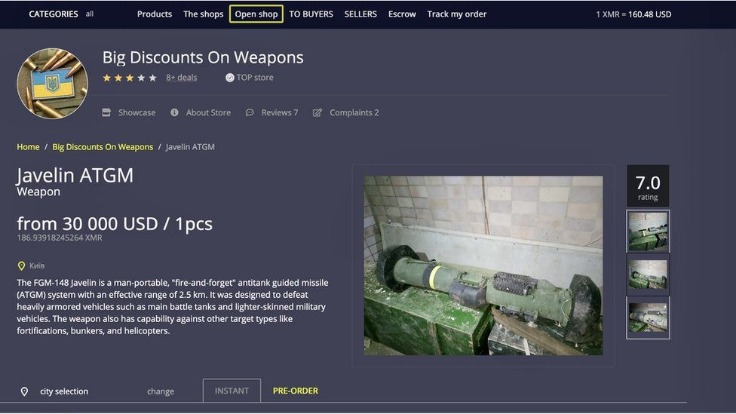
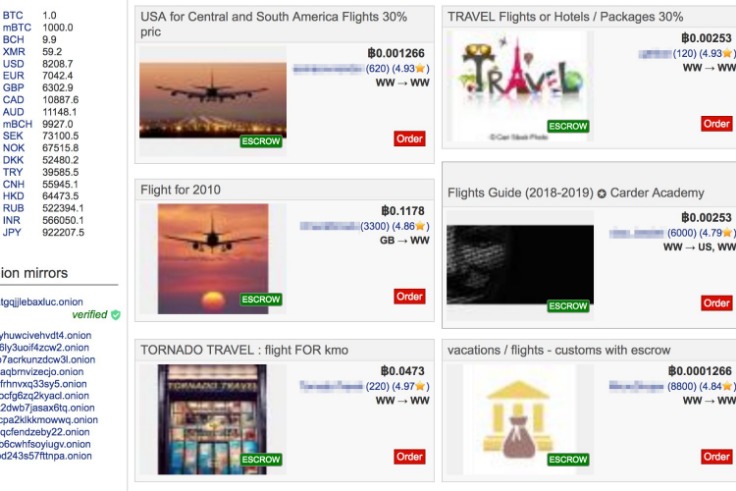
Crucially, she also outlines what service providers—including telcos, financial services, and insurers—can do to help protect consumers from carding in today’s shifting cyber threat landscape. Once you find a forum or market that offers the service you’re looking for — such as stolen passports — signing up for them is not unlike creating an eBay account. The main difference is that purchases are made with cryptocurrencies, and quite often such sites are far more secure than their clear web counterparts. Passphrases, distributed denial-of-service (DDoS) protection pages, and multifactor authentication are all quite standard on many darknet marketplaces.
- There’s a wealth of information shared among carders—from how to bypass anti-fraud systems to practical guides on using stolen credit cards—all of which helps keep the ecosystem active and evolving.
- Criminals can easily sell stolen credit card information to other malicious actors on the dark web, leading to potential financial devastation for victims.
- Though the vendor is still online and has blamed the issues on “technical difficulties”, it has been banned and removed from all high-profile cybercriminal forums following a major row in June.
- Unlike the traditional web we use every day, with search engines indexing websites for easy discovery, the Dark Web operates on anonymous networks such as Tor.
- Becoming familiar with their techniques can help you retain control over your money.
Resolving an unauthorized transaction involves opening a claim with your card provider, which may result in an investigation and a potentially lengthy chargeback process. We will also share some effective safety tips and discuss how virtual cards can help protect you from card fraud. Join us as we break down and discover the methodologies of card fraud using our dark web monitoring tool, Lunar.
- Dark web credit cards are often sold on online marketplaces, which can be accessed through specialized browsers like Tor.
- With stolen payment cards, a cybercriminal can immediately make purchases under your name, or even drain your bank account.
- I’ve seen cases where security teams identified compromised card data from their institution appearing on the dark web weeks before they traced the actual breach point.
- Unless you live the rest of your life only paying with cash, you’ll never be totally impervious to payment fraud.
- The dark web has become a hub for credit card fraud, making it a significant concern for both individuals and businesses.
- For instance, cybercriminals can buy credit card details with a $5,000 balance for just $110.
The use of JavaScript-sniffers, also known as Magecart, has led to a significant increase in stolen payment card data. A second major leak of cards relating to Indian banks has been detected by Group-IB, with over 1.3 million credit and debit card records being uploaded to the Joker’s Stash marketplace. Thank you for joining us on this exploration of credit card transactions on the Dark Web. Stay vigilant, protect yourself and others, and make ethical decisions when navigating the vast landscape of the internet.
People unexpectedly have their card cloned, their identities stolen, or their accounts hacked. Most stolen card details end up on the dark web marketplace for a quick profit, and this can happen before you even know about it. Dark web credit card numbers are stolen card details sold on hidden websites. Leaked credit cards from Telegram channels account for the overwhelming majority of compromised payment card details. Accessing the dark web exposes you to several potential security risks.
Types Of Stolen Cards
Some vendors offer a “complete package” known as “Fullz”, which includes full personal details as well as financial details like bank account information or social security numbers. The ease of access and navigation of Telegram carding groups is a major concern, as it allows cybercriminals to easily buy and sell compromised payment card details. Free and paid tutorials on the dark web teach fledgling criminals how to use stolen credit cards. If you come across any instances of credit card fraud or encounter suspicious activities, it is essential to report them to relevant authorities. By doing so, you can contribute to mitigating the impact of these illegal activities and help protect innocent individuals from falling victim to financial fraud. Remember, while evaluating seller feedback and ratings can provide valuable insights, engaging in credit card transactions on the Dark Web is illegal and carries significant risks.
Good Password Ideas And Tips For Secure Accounts
The data posted on these online illicit shops is a goldmine for threat actors who are looking to commit financial crimes. It provides them with valuable information needed to carry out a variety of attacks. All of these features, its competitive pricing, along with the volume of credit card information listings, make Real and Rare one of the prime sites to trade credit card information online.



