
All information, including rates and fees, are accurate as of the date of publication and are updated as provided by our partners. Some of the offers on this page may not be available through our website. Experian is a globally recognized financial leader, committed to being a Big Financial Friend—empowering millions to take control of their finances through expert guidance and innovative tools.
- What makes these tools particularly concerning is their accessibility.
- On November 7, 2024, Finastra, a London-based financial technology company, detected unauthorized access to its secure file-transfer platform.
- Improve your online security by creating strong, unique passwords for your online banking and shopping accounts, using a password manager, and enabling multi-factor authentication (MFA) wherever possible.
- These measures include implementing robust security practices, such as encryption and multi-factor authentication, to protect credit card data and reduce the likelihood of it ending up on the dark web.
- This tactic mirrors similar marketing stunts by other illicit platforms, such as BidenCash, which leaked 2 million cards in 2024 to celebrate its anniversary.
- Those details are useful for tactics like spearphishing specific people to try to steal their login credentials for personal or work accounts, researchers say.
Methodology And Prevention

A fair number of vendors include access to a SOCKS5 internet proxy that can be used by the buyer to match their computer’s IP address location with that of the cardholder in order to avoid being blacklisted. By clicking “Continue” I agree to receive newsletters and promotions from Money and its partners. I agree to Money’s Terms of Use and Privacy Notice and consent to the processing of my personal information. One of the largest known underground shops, Joker’s Stash, generated more than $1 billion before getting shut down in February, according to Gemini Advisory. A 2019 data leak of another shop, BriansClub — which appears to have been by a competitor, according to Threatpost —shows how pervasive this trend has become. He said it felt more like a “victimless crime” because he thought most people would end up getting their money back anyway.
How To Use Privacy Cards

The IMF responded by securing the accounts, enforcing multi-factor authentication, and boosting employee cyber awareness. This cyber incident joins the list of latest data breaches that show how a single point of failure can threaten sensitive data. Luxottica agreed to a $250,000 settlement following a data breach that exposed personal and health information of over 829,000 eye care patients in August 2020. The breach stemmed from unauthorized access to an appointment scheduling system and included names, health data, financial information, and Social Security numbers. Over 184 million login credentials tied to Google, Apple, Microsoft, Facebook, Instagram, Snapchat, and other platforms were exposed in a major data breach, according to the New York Post. Cybersecurity researcher Jeremiah Fowler found the database sitting online without encryption or any password protection.

Protect Yourself From Tax Scams
The breach remained undisclosed for a year, leading to fraudulent charges on customer accounts. Well, it is mostly misused by attackers for their criminal activities or it ends up on the dark web for sale. Cybercriminals often use the stolen financial data to make fraudulent purchases online or to compromise other accounts via credential stuffing attacks. Most scammers obtain credit card numbers and other financial data from various darknet forums.
Dark Web Credit Card Numbers: Understanding The Risks And Fraud
- While ByBit’s CEO Ben Zhou emphasized that no customer funds were affected and the firm has replenished the stolen amount through investor loans, the company launched a Lazarus Bounty program.
- In most cases, actors post the details of a limited number of stolen cards as a way to advertise that they have a larger and constant stream of fresh cards available for purchase.
- To pull off these credit card scams, D2 and other fraudsters would sign onto sites on the dark web and simply pay a small fee—as little as $35 — for victims’ credit card information.
- WK Kellogg is offering one year of identity theft protection through Kroll.
This tactic mirrors similar marketing stunts by other illicit platforms, such as BidenCash, which leaked 2 million cards in 2024 to celebrate its anniversary. The pausing/closing feature is especially useful if a specific Privacy Card has been exposed in a data breach or you want to block hidden/unwanted subscription charges. Keep in mind that you still need to reach out to the subscription provider if you’d like to cancel the service. If you notice suspicious activity, you can pause or close your virtual card in a few clicks—–via either Privacy’s web app or mobile app—and Privacy will decline any subsequent payment requests on the card. You won’t have to block and replace your actual payment card, which is often a complicated and lengthy process.
Why Physical Security Maintenance Should Never Be An Afterthought
Japan, the UAE, and Europe have the most expensive identities at an average of $25. Due to limited data on credit cards from other countries, we were unable to adequately compare prices for credit cards from different places. You can also limit your risk by being picky about your ATMs, where criminals sometimes install card skimming devices. These are hard to detect, but only using ATM machines inside banks or other physical buildings offers some protection, Thomas says. Sometimes hackers will commit “card-present fraud” by breaching the point of the sale at a physical store.
Over 30 Million Stolen Credit Card Records Being Sold On The Dark Web
Credit cards, Paypal accounts, and fullz are the most popular types of stolen information traded on the dark web, but they’re far from the only data worth stealing. Sales of passports, driver’s licenses, frequent flyer miles, streaming accounts, dating profiles, social media accounts, bank accounts, and debit cards are also common, but not nearly as popular. Unlike a credit card, a debit card is connected directly to your checking account, allowing fraudsters to immediately drain your account. Even if you report the fraudulent activity quickly and limit your losses, you may still face the issue of bounced checks or being late on payments, Krebs says. With stolen payment cards, a cybercriminal can immediately make purchases under your name, or even drain your bank account.
Category #2: Details Needed For Physical Fraudulent Use
These measures include implementing robust security practices, such as encryption and multi-factor authentication, to protect credit card data and reduce the likelihood of it ending up on the dark web. You’re probably wondering how things like a PayPal account login or credit card details end up on the dark web. People unexpectedly have their card cloned, their identities stolen, or their accounts hacked. Most stolen card details end up on the dark web marketplace for a quick profit, and this can happen before you even know about it.

Understanding Credit Card Fraud On The Dark Web
The company has also reported the incident to federal law enforcement and regulatory authorities. Home Depot had to pay a hefty price for the breach, with $25 million going to banks, $134.5 million to card companies like Visa and MasterCard, and $19.5 million to affected customers. The hacker was later caught and jailed, but not before five people, including the hacker, were indicted for attacking various retailers, financial institutions, and payment processing firms. I can’t say for certain, but I’ve always seen carding as a more ‘hardcore’ form of cyber crime—at least from a criminal’s perspective. Compared to harvesting phone numbers or email addresses, carding demands more risk, and potentially, more reward.
By monitoring the dark web, you can quickly identify when your cards are compromised through partner organizations or merchants. When used correctly, it provides strategic intelligence that can prevent major financial losses. I’ve investigated too many breaches where malware jumped from an infected office computer to the payment network. Network segmentation is absolutely critical for businesses handling card data.
However, the validity of the data hasn’t been confirmed yet, so it could very well be auto-generated fake entries that don’t correspond to real cards. Follow our recommendations to secure your information, such as notifying your bank and updating security settings on your accounts. We monitor your Equifax credit report, provide you with alerts, and help you recover from ID theft so you can focus on living your financial best.
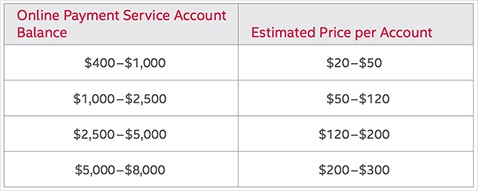
In 2019, Capital One experienced a major data breach that exposed the personal information of more than 100 million U.S. customers and an additional 6 million in Canada. The breach was caused by a misconfigured firewall in their cloud setup, not by a sophisticated cyberattack. The attacker was able to access names, addresses, social security numbers, credit scores, and linked bank account details. Legitimate users of the dark web include activists, or people who live under oppressive regimes, but they only account for a small percentage of the dark web. The sale of payment card information is big business; in 2022, the average price of stolen credit card data averaged between $17 and $120, depending upon the account’s balance. The black market for stolen credit cards is a massive illegal business, with cybercriminals getting their hands on card data in a number of ways.
Bank Sepah Data Breach
Learn the basics of credit card cards, including features, fees, and rewards to make informed decisions about your credit card usage. The price for cloned cards varies depending on the credit limit, with an average price of $171. Telegram carding groups have become a significant threat in the cybercriminal community, with tens of thousands of members easily accessible through the chat application.
One of the most recent and devastating cyberthreats facing merchants is the rise of Magecart hackers, according to Mador. These groups of cybercriminals have been very active in the past two years, stealing credit card data by injecting malicious code into the checkout pages of merchants’ e-commerce stores. Magecart groups have been operating since 2015 and are believed to have compromised nearly 50,000 e-commerce sites since then, according to the Trustwave report. Dark Web Monitoring scans known dark web forums, marketplaces, and breach databases for stolen or leaked credit card information. When your card details are found, we immediately send an alert, allowing you to quickly take action, such as freezing your account or updating your card information. These criminals released the details of 740,858 credit cards, 811,676 debit cards, and 293 charge cards.



