
However, we advise connecting to one of our recommended VPN services to stay anonymous. The Tor network was created by the US military in the 1990s for anonymous communication between spies over the internet. That effort was never fully realized, but the US military published the code under a free license in 2004. Researchers from the Electronic Frontier Foundation and other groups continued its development and launched the Tor project in 2006 as a tool for journalists, activists, and whistleblowers. For built-in Tor over VPN functionality, NordVPN operates specialized servers that automatically route you through the Tor network. You don’t even need to use Tor Browser, but keep in mind other browsers can still pass identifying information through the network.
What Is The Dark Web? How To Access It Safely?
These can include the previously mentioned illegal offerings, but can also include ultra-private information designed to be shared only with certain parties. There’s a significant risk to dark web users of being exposed to malware (malicious software) infections. There are several programs that hackers frequently use on the dark web.
Meanwhile, cybersecurity experts monitor the dark web, scanning for stolen data and emerging threats. If your information surfaces in these murky depths, there’s very little you can do – but knowing the risks involved is a first step toward defence. From information security threats like identity theft and malware to scams and surveillance, navigating the dark web without caution can lead to real dangers. So, is the dark web a lawless underworld or a misunderstood frontier for privacy and free expression? Additionally, much of the materials on the dark web are illegal, and unknowingly downloading such content can implicate you in criminal activities punishable by laws. If your device is infected with malware, read our guide to remove malware from your computer.
What Is The Role Of Relays In Tor?
At the time, the internet was still young, and tracking people was easy while staying anonymous was not. The Tor network allowed safe communication channels for political dissidents and American intelligence operatives around the world. Fraud and scams run rampant on the dark web, including offers too good to be true and fake services requiring upfront payment. Hackers sell access to email accounts, social media profiles, or other information that can be used for identity theft. As always, protect yourself from online threats with mobile Android security or iOS security software.
Is It Legal To Browse The Dark Web?
The encrypted data, such as WhatsApp messages, are secured behind end-to-end encryption and are not visible to your ISP. It means unless you use a VPN that encrypts your internet traffic, they always receive all information about you and your digital life. Your Internet service provider, or ISP, is your gateway to the Internet. While a website can’t identify you or an ISP can’t decrypt your internet traffic; still, they can still see you using Tor, which can draw some unwanted attention and raise suspicions. Many countries, such as Qatar, China, Cuba, Russia, and Turkey, censor internet content promoting political dissent. The Darknet offers a place of free expression where not even a chunk of these limitations exists.
Many people (mostly criminals) use these sites to perform illegal transactions such as selling banned goods and services. Therefore, you must know how to access dark web marketplaces safely (covered later in this article). If you connect to your VPN and fire up Tor Browser, you’re using Tor over VPN. All your device’s internet traffic first goes to the VPN server, then bounces through the Tor Network before ending up at its final destination. Your ISP only sees the encrypted VPN traffic and won’t know you’re on Tor. A logless VPN, which doesn’t store any traffic logs nor session logs is highly preferable.
Market Value And Popularity
There are reports of illegal services on the dark web, ranging from paid assassinations to the trafficking of sex and weapons. However, some of these alleged services, such as professional ‘hitmen,’ may be scams designed to defraud willing customers. For your optimum dark web safety, you should ensure that once you’re done browsing the Darknet, shut all the browser windows as well as any other content that could be connected. NordVPN has a strict no-logs policy to ensure user privacy and employs 256-bit AES encryption. It is also available on various operating systems, including Linux, Windows, MacOS, iOS, and Android. However, it’s important to note that NordVPN can see your traffic details before encrypting them, even though it does not keep logs.
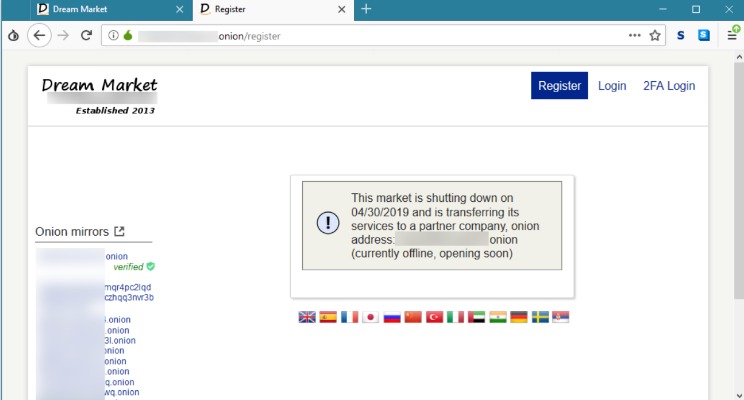
Can I Get In Trouble For Accessing The Dark Web?
Because it’s easier to contain malware in a virtual environment, which can be fully controlled. There’s no broad consensus on dark web safety, but you at least need to use Tor and VPN together. Once you have those, there are several ways to tunnel through the dark web. Tor relays are servers run by volunteers, designed to keep your activities private and untraceable. Navigating the dark web requires extra layers of privacy, not just because of its content but due to legal scrutiny. The US Supreme Court has indicated that even casual browsing could lead to legal consequences.
How To Access Onion Sites
So, you should never share your personal information on the dark web. What’s more, they can also sell you personal information on the dark web as your personal data has a monetary value on the dark web. The dark web is a playground for hackers, cybercriminals, and people with nefarious objectives.
All are fine as long as they can retrieve information from the non-indexed dark web and protect your privacy. Some popular search engines that can help you explore hidden content and anonymize your web traffic include DuckDuckGo and Ahmia. Many people use Tor to avoid surveillance by government agencies, ISPs, or other entities monitoring online activities. Similarly, people in countries with strict internet access and usage regulations must use Tor clients or virtual private networks (VPNs) to access some public websites. In principle, the dark web is just a version of the internet that you can only access using a Tor browser and where it’s almost impossible to identify the users and owners of the websites on there.
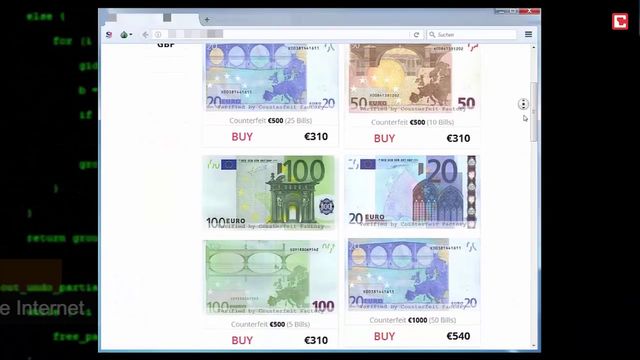
This extra privacy makes it much harder for authorities to track down who runs these markets and where they are located. For these reasons, most of these stores naturally like the dark web due to its protection. The node requests the data from this server and forwards it to the user. This means that it is not possible to find out where the server is actually located using conventional means.
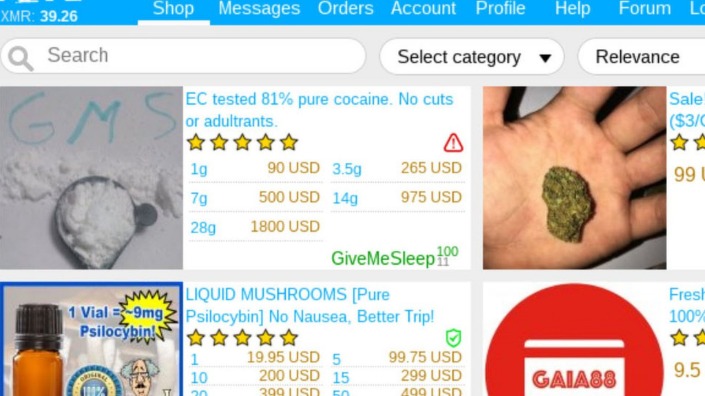
What Is A Darknet Market?
Most search engines do not work on the dark web, because they are not designed to search for “.onion” URLs. The good news, however, is that you can use the dark web version of DuckDuckGo to search for and navigate to websites on the dark web. Whether you are accessing your email account, private backups, or your credit card statements, that data is stored on the deep web. Due to the value of the private data that is stored on the deep web, it is vital that it is always secured extremely well using encryption. Tor browser is named after “The Onion Router” protocol that powers the dark web.
- The dark web hosts numerous sites explicitly designed to distribute malware.
- This handy feature monitors the dark web for signs that your login details or other personal info have been leaked.
- At KELA, we help you identify and mitigate risks by providing actionable intelligence from the darknet.
- The most prevalent dark web content is child pornography, about 80% of its web traffic, despite being challenging to find.
- Surfshark is a low-cost provider that ticks all the boxes for use with the dark web.
This is another reason it’s best to use a VPN and be careful on the dark web to preserve anonymity. A lot of the user data that gets stolen or leaked from big platforms ends up on the dark web, where users buy, sell, and exchange it among themselves. A phishing website or link is one that appears legitimate but is actually a trick designed to make you hand over your personal information to hackers and other bad actors. Often, these sites are made to look just like real, trusted platforms, such as banks, social media sites, or email providers. However, there are also perfectly legal, safe sites within the dark web, like privacy-focused forums, marketplaces, and more.
The dark web is home to plenty of unlawful activity, so you must ensure you never get involved in something illegal. While connected through NordVPN, your internet traffic is protected using AES 256-bit encryption. NordVPN adheres to a strict no-logs policy, which has been twice verified by independent auditors. This allows you to use public WiFi privately and without fear of hacking. There’s no chance of your real IP address leaking, while it benefits from some of the fastest speeds on the market. Using a VPN in conjunction with the Tor (The Onion Router) browser is the best way to access the dark web safely.
- It leaves no digital footprint on your primary system, ensuring your activities can’t be traced back to your regular devices.
- Download the Linux version from torproject.org, extract the file, and run the start-tor-browser script.
- We already know of one necessary component needed for this – Tor.
- We’re back with another video in our Webz Insider video series on everything web data.
- That information is hidden simply because most users won’t find it relevant.
- In fact, research performed at the University of Kent in 2015 revealed that 57% of the dark web hosts illicit material.
A study by researchers at King’s College London that examined the contents of over 2,700 darknet sites found that approximately 60% of them hosted illicit content. If you’re interested in marketplaces, start by learning about the top darknet markets. These platforms are hubs for various services and goods, and understanding their features is key to navigating them safely.



